Managed and Support Services
ADResQ | Active Directory Rescue Service

ADResQ |
Active Directory Rescue Service
Attacks are guaranteed. Is your recovery?

84% of organizations report that the AD outage would be catastrophic
The average time due to downtime is 21 days

Only 37% of organizations understand the complexity of AD forest recovery
Is the threat of ransomware keeping you up at night in spite of your best efforts to protect your company?

No organization is immune to cyber attacks, especially the increasingly sophisticated ransomware that’s cropped up in the past two years. But you can mitigate operational, financial, and reputational consequences with proactive ransomware recovery services. If you’re locked out of your systems, the first thing you’ll need to recover is Active Directory (AD). Standard AD Disaster Recovery (DR) plans are not always effective against ransomware.

Restore AD, Restore Power.
At Itergy, we offer you a proactive Active Directory ransomware recovery solution that guarantees your AD will be back up and running in a matter of hours. Our reliable solution combines extensive AD expertise, a proprietary methodology, best-of-breed tools, and auditable recovery testing. We’ll restore your Active Directory to clean domain controllers, minimizing the risk of entering a reinfection loop.
We, at Itergy, guarantee AD recovery in under 4 hours in any ransomware scenario, no hassle, just results! Let us take this burden off your IT team so you can focus on what truly matters.
Are you ready to recover Active Directory from an inevitable ransomware attack?
Today, standard backups of Active Directory are simply not enough. Recovering AD from ransomware can be extremely challenging. Have you tested your DR plan for gaps or errors?
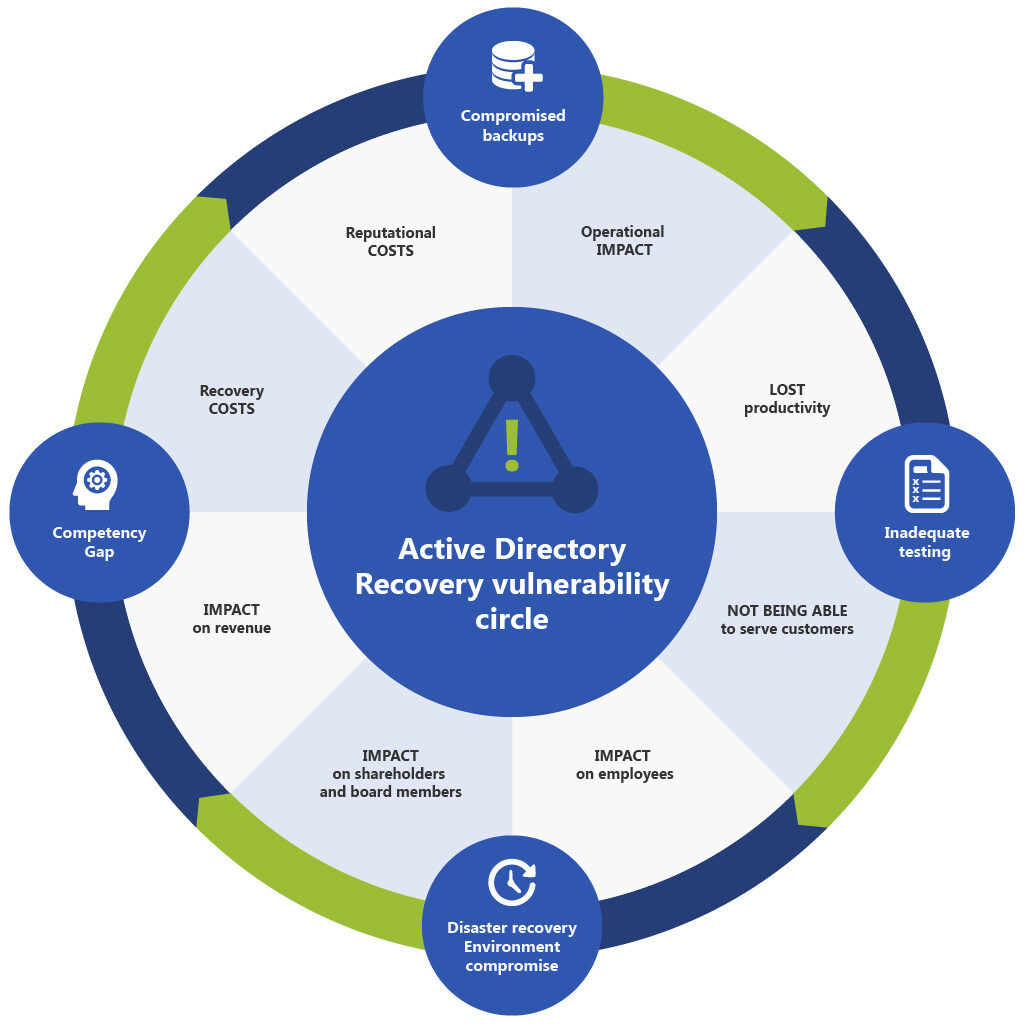
Ransomware Risks
Competency Gap
The cybersecurity talent shortage is compounding the crimeware problem. Finding Active Directory experts with field experience in ransomware recovery is hard. You need a team you can count on to:
- Establish an AD specific methodology
- Put the right AD backups processes in place
- Maintain internal SLAs against security threats
Once AD is compromised, nobody can log in. An Acitve Directory Recovery after a ransomware attack is not as simple as clicking the “restore” button. It requires a precise series of exact steps and the right tools. Otherwise, you risk destroying the entire Active Directory forest. Can you imagine the impact this would have on your business?
Compromised Active Directory Backups
By the time you’re locked out of your systems, hackers have probably been studying your networks for months.
They’ve had ample time to encrypt or tamper with your backups – or worse, delete them. As a result, malware is almost certainly lurking in your backups, just waiting to be reactivated. Finding AD backups that are not affected can take days, if not weeks.
One way to mitigate this risk is to treat AD backups separately from other systems. Storing them in a highly secure location, inaccessible from your current environment, can keep them safe.
Compromised Ransomware Recovery Environment
Hackers may also try to access your Disaster Recovery environment and force you into a reinfection loop. What is your fallback plan if you’ve introduced malware to your OS and your DR environment is also compromised? Restoring Active Directory separately from your other systems to a clean, on-demand, high-availability environment can save the day.
Inadequate Testing of Active Directory Ransomware Recovery
The weakest link in the recovery scenario is the restoration process. And yet, many DR plans are untested or inadequately tested.
Testing Active Directory restoration independently from other systems is essential, as it often reveals vulnerabilities or broken processes. Who would be held accountable for a failed recovery caused by flaws in your AD Disaster Recovery plan?

It is not a matter of “if”, but “when”
Active Directory literally holds the keys to your kingdom. Therefore, establishing an AD-specific recovery and Disaster Recovery plan to address these vulnerabilities is essential.
Readiness evaluation: Have you made Active Directory Disaster Recovery a priority?
Use these questions to analyze your current practices. Does anything set off alarm bells?
- When you developed your ransomware backup and recovery processes, did you treat AD separately from your other systems?
- Can you guarantee your key stakeholders that you can recover the ability to log on to computers in four hours or less after a ransomware attack? If so, how is that enforced?
- What would be the impact on employees, productivity, revenue, reputation, and, most important, on your customers if no one could log on to their computers for several days?
- Do you have a plan in place to protect Active Directory backups from tampering, encryption, or deletion?
- Have you tested AD recovery scenarios to uncover flaws in your DR processes so that when an incident happens, you can recover quickly?
- How long would it take you to recover Active Directory separately from other systems in the event of catastrophic failure?
- If you could not recover your AD, how long would it take you to rebuild it from scratch and repopulate it?
Downtime and Recovery Cost Calculator
Build your business case with our ransomware cost calculator.
ADResQ | Our AD Ransomware Rescue Service
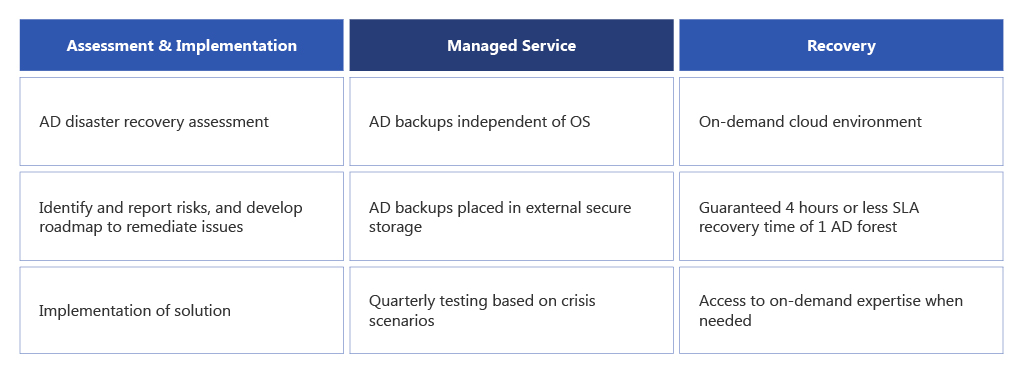
Combining our extensive Active Directory expertise, proprietary methodology and tools, we’ve built a proactive AD recovery solution that guarantees you’ll be back up and running in four hours or less in case of ransomware. Our solution is divided into three components:
Key Benefits
Minimize Downtime and Business Disruption

Reduce Risk of Backup Encryption, Infection or Deletion

Access to deep Active Directory expertise

Fast Implementation

Mitigate Possibility of DR Environment Compromise

Proprietary Tool and Unique Intellectual Property

You need a solution and you need it now.
Building a solution like this usually requires months of work and, most importantly, deep Active Directory expertise and experience recovering Active Directory from ransomware catastrophes. Our solution is designed to fit right in and strengthen your cybersecurity roadmap. Best of all, it can be implemented in four weeks or less. Hackers won’t wait, so why should you?